-
 Disaster Recovery as a Service DRaaS is a combination of Service Levels designed to offer comprehensive protection for your Organization through any concievable event. VMsources can have your entire IT infrastructure protected in less than a week! Give us a call and we'll schedule you right away!
Disaster Recovery as a Service DRaaS is a combination of Service Levels designed to offer comprehensive protection for your Organization through any concievable event. VMsources can have your entire IT infrastructure protected in less than a week! Give us a call and we'll schedule you right away! - Onsite Incrimental Backup facilitates fast administrative restores
- Offsite Backup protects your data outside your Organizational Active Directory and keeps it safe from Ransomware
- DRaaS Replication provides a ready-to-power-on Replica VM of all your mission-critical systems, which keeps Recovery Time Objective (RTO) as low as possible
Our DRaaS Secure Cloud is designed from the ground up to provide the highest level of Business Continuity attainable anywhere, and with one important goal: to protect your data. From best-of-breed servers to fully redundant infrastructure, VMsources SecureCloud provides effective, verifiable Disaster Recovery solutions customized to suit our clients specific needs, including our famous Concierge Service at no extra charge.
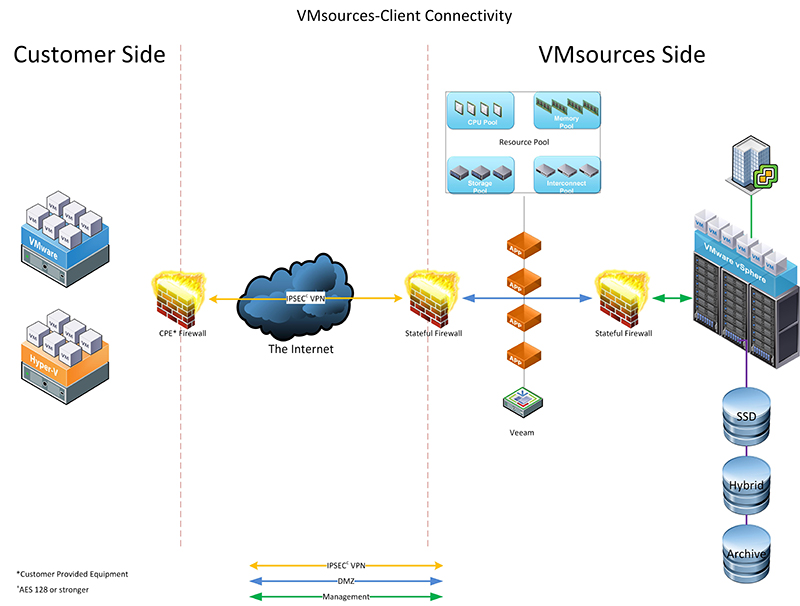
Network Bubble
One of the most important aspects of VMsources' Disaster Recovery is our ability to exactly replicate your entire production network. Our disaster recovery plans allow you to run all of your protected servers and desktops as they are, without changing IP addresses relative to one and other.
- VMsources VPN appliance insures efficient and secure transmission of data over any internet connection.
- VMsources has disk-based solutions with FedEX – no bandwidth required!
- VMsources partners directly with Veeam so we can utilize their replication technology which features inline compression and deduplication so you get faster R.T.O. and reduced bandwidth consumption!
With all of the resources we already have in place, and all of the processes we have licensed and mastered; we could literally, seed the data today [2] and by tomorrow night you would have a White Glove Disaster Recovery plan in place!
Here’s how Disaster Recovery works:
- We will create a Guaranteed TCO quote for your DRaaS Protection.
- We create a secure IPsec VPN connection from your location to our datacenter.
- VMsources Business Continuity specialists work with your Admins to Seed of all of your Organizations mission-critical systems to our Secure Cloud.
- We establish scheduled replication with Veeam Backup and Replication.
- We create a DR Plan, customized to your Organization and provide comprehensive training on how to run or test your DR plan.
- We help you test your DR plan, and provide documentation of the successful test.
- In the event of an actual disaster, your protected Servers/VMs/Computers will power up relative to one and other, just as they are set up to be – no IP reconfiguration on the servers themselves!
- VMsources can help you update your public DNS, or we can help you automate the process of updating DNS in the event of a disaster.
Technical Advantages
- 10 Gigabit Port on a dedicated fiber loop
- 100% optical connection to the Internet Backbone
- 42 ms. Intra-USA latency (Guaranteed by Cogent SLA)
- 99.9995% Uptime
- Unique, isolated and firewalled network(s)
- Port forwarding configured & tested in advance
Geographic Advantages
- Nationwide Compute and DRaaS nodes.
- Tier 4 Datacenter
- 100% Facility SLA
Service Advantages
- VMsources will create the VPN (equivalent to MPLS) and guarantee latency/throughput
- We will assist with initial replication – “seeding”
- VMsources will monitor/maintain DR side of the house
-
 Your Organization needs and likely requires meaningful Auditing and Compliance Reporting for your Information Systems and Information Technology deployments.
Your Organization needs and likely requires meaningful Auditing and Compliance Reporting for your Information Systems and Information Technology deployments.
But are you making that happen? And why is a robust auditing and compliance practice one of the most sought-after but least-attained goals?
Our approach is to make compliance assurance and auditing reporting easy. All of our Cloud Solutions include 100% adherence to the latest standards and practices.
VMsources first attained compliance with AICPA SOC 1 and SOC 2 in 2014. Since that time, we have continually added compliance and auditing standards through our partnership with CoreSite. As of 2021, we are pleased to announce full compliance with the highest standards in Data Center Compliance, Certification and Security.- If you utilize any of our DRaaS / Business Continuity Solutions, you have the assurance that your data is priotected by the highest ndustry standard compliance requirements.
- When you migrate active workloads to our Secure Cloud, they automatically become part of our Auditing and Compliance and DRaaS / Business Continuity Solutions is protected as well!
Each year, an external auditing firm completes System and Organization Controls (SOC) 1 Type 2 and SOC 2 Type 2 reviews of our data center facilities. The reports provide our customers with the assurance of corporate controls, including security and environmental compliance, and validation of CoreSite's commitment to the most stringent standards of excellence in our data center operations. SOC 1 Type 2 and SOC 2 Type 2
SOC 1 Type 2 and SOC 2 Type 2
SOC 1 and SOC 2 are attestation standards issued by the American Institute of Certified Public Accountants (AICPA). The SOC 1 report is intended to meet the needs of user entities’ management and auditors as they evaluate the effect of a service organization’s controls on the user entity’s financial statement assertions. The SOC 2 report is intended to meet the needs of a broad range of users that need to understand internal control at a service organization as it relates to security, availability, processing integrity, confidentiality, and privacy. CoreSite’s SOC 2 reports include the security and availability Trust Services categories.
CoreSite has achieved the International Organization for Standardization certification (ISO 27001) covering both corporate policies and procedures, as well as those of all our operating data centers. The ISO/IEC 27001:2013 certification is one of the most stringent certifications for information security controls, and confirms the information security controls and other forms of risk treatment are in place to detect and defend against potential data system vulnerabilities. This prestigious, internationally-recognized certification reflects our commitment to provide CoreSite customers around the globe with secure, reliable, and high-performance data center colocation hosting solutions. ISO 27001
ISO 27001
Each year, an independent Third Party Assessment Organization (3PAO) firm completes an external assessment to validate CoreSite’s strict adherence to the National Institute of Standards and Technology Publication Series 800-53 (NIST 800-53) high-impact baseline controls and additional Federal Risk and Authorization Management Program (FedRAMP) requirements. The scope of CoreSite’s assessment includes a subset of control families applicable to colocation services at our data center facilities. The utilization of the high-impact baseline controls for NIST 800-53 reflects CoreSite’s commitment to successfully delivering the most rigorous compliance standards to support our customers’ Federal Information Security Management Act (FISMA) and FedRAMP compliance efforts. NIST 800-53
NIST 800-53
NIST 800-53 is a publication that recommends security controls for federal information systems and organizations. NIST 800-53 is published by the National Institute of Standards and Technology which creates and promotes the standards used by federal agencies to implement FISMA and manage other programs designed to protect information and promote information security.
Each year, a Quality Service Assessor (QSA) completes an external assessment to validate CoreSite’s compliance with the Payment Card Industry (PCI) Data Security Standard (DSS) as a “Level 1” service provider for our colocation services. The scope of CoreSite’s assessment includes physical security and related policies at our data center facilities. PCI DSS
PCI DSS
The PCI DSS is a comprehensive set of standards that require merchants and service providers that store, process, or transmit customer payment card data to adhere to strict information security controls and processes. As a provider of data center colocation services, CoreSite has proactively met the relevant requirements for its business in support of the PCI compliance needs of its customers.
HIPAA requires that covered entities take strong measures to protect the privacy and security of electronic protected health information (ePHI). By attaining HIPAA validation through an external attestation, CoreSite provides assurance to healthcare providers and other related enterprises that its national platform of multi-tenant data centers conforms to a high standard of data security and provides a secure environment for customers’ sensitive and confidential data. HIPAA
HIPAA
The validation asserts that the information security program governing the colocation services implements applicable control guidance in the HIPAA Security Rule and the Health Information Technology for Economic and Clinical Health Act (HITECH) Breach Notification requirements.
-
 Protect your Organization from Ransomware, Disasters and Cyber Attacks with a full range of best-of-breed Business Continuity solutions designed specifically to keep your data available, up-to-date and completely secure.
Protect your Organization from Ransomware, Disasters and Cyber Attacks with a full range of best-of-breed Business Continuity solutions designed specifically to keep your data available, up-to-date and completely secure.
- Business Continuity Terms
- Disaster Recovery DRaaS
- Fully Managed Backups
- Secure Offsite Backup
- True Offline Backup
- Fixed Cost S3 Backup
Business Continuity FAQ:
Q: How does VMsources pricing work? Are there hidden charges?A: We have the easiest to understand pricing you will find anywhere, and we are the ONLY provider offering a guaranteed TCOfor your Secure Offsite Backup or DRaaS protection!-
- We charge for actual space used by Backups or Replicas at some of the lowest rates in the industry.
- We have Veeam Backup and Replication available as SaaS/Rental so you pay only for what you use, while you are using it.
There are never any ingress, egress, Block Blob or other hidden surcharges to access or use your data. Plus, our famous Concierge Service is included for every customer/job, no matter how small or large!
Q: What advantages does VMsources provide over the Big Cloud like Azure or AWS?A: Personalized service, guaranteed TCO, 100% USA-based support.
Q: How quickly can VMsources protect my environment with Secure Offsite Backup or DRaaS?A: In just a few days.
Q: How does VMsources Secure Backup protect our organization from Ransomware?A: First and foremost, our backup systems are entirely separated from your Organizational AD, so Threat Actors will not have the ability to exploit credentials to gain access. Secondly, we use Veeam Hardened / Immutable Repositories to prevent any changes to data after it is written.
Q: What’s the 3-2-1 Backup Rule?A: The 3-2-1 Backup Rule requires three (3) copies of your data on two (2) devices with at least one (1) copy offsite.
Q: How does VMsources implement the3-2-1 Backup Rule?A: We create a local Backup job, a Backup Copy job and a Replication job to protect your mission-critical data. Three (3) copies are:- The local Backup, the offsite Backup, and the Replica.
- Two (2) devices are the local backup repository and the offsite backup repository.
- The one (1) copy offsite is either the Replica VM or the offsite Backup.
A: VMsources will provide a Backup and DR Certificate of Compliance confirming compliance and the compliance period.
Q: How do I know if my Backup jobs are running successfully?A: VMsources monitors your jobs and will notify you if there is an issue.PLEASE NOTE: Many providers simply provide you instructions on how to setup notification – VMsources takes a more active role and makes sure you know if there is a problem with protection.
Q: If I have Secure Offsite Backup, can I restore my VMs, Servers or PCs to the Secure Cloud in the event of a disaster?A: Yes. You can restore them to VMsources Secure Cloud or any other cloud hosting service!
Q: Can I do Secure Offsite Backup without DRaaS Replication, but convert my Secure Offsite Backups to the Secure Cloud in the event of a disaster?A: Yes, but the restores may take some time to complete, so it’s not recommended for low Recovery Time Objective (R.T.O.) scenarios. Also, with Offsite Backup, compute resources pre-provisioned on-demand and may not be available at the exact moment you need them.
Q: What is the advantage of having DRaaS Replication in addition to Secure Offsite Backup?A: DRaaS Replication provides a ready-to-run replica provisioned in our Secure Cloud. This accomplishes two important goals: RTO is drastically reduced and Secure Cloud resources are reserved in advance for your Organization.
Q: What’s the RTO if we implement DRaaS Replication to the Secure Cloud?A: The VMs will be available almost immediately after a disaster or for a DR test. How long it takes your organization to update DNS and re-connect users can vary widely.
Q: How do we execute DR Tests is we have DRaaS Replication with VMsources?A: VMsources will have first created a custom DR Plan for your Organization. As part of our famous Concierge Service, a VMsources Business Continuity specialist will help you to execute your DR Plan and document the successful results or adjust the DRaaS protections and/or DR Plan until we achieve total success.
Q: Does a DR Test cost anything?A: NO, VMsources does not charge for running DR Tests, either for out time or the Secure Cloud Compute used during the test.PLEASE NOTE: Most providers do not assist you during tests and will charge extra for Cloud resources consumed during the test.
Q: How many VLANs/Networks/DMZs can I have?A: We place no limit on that. Additional VLANs/Networks/DMZs are provided at no cost.
Q: How many public IP addresses do I get?A: We have no set limit to the number of IP addresses you can have. We assign a minimum of one public IP for all Secure Offsite Backup and DRaaS clients.
DRaaS clients with replication will get pre-assigned static public IP addresses for each of their public services, such as: Mail, Web, VDI, etc. These pre-assigned static public IP addresses will remain yours for the life of the SolutionPLEASE NOTE: Most providers assign public IP addresses from a “pool” as failover is performed, so there is no possibility of pre-arranging whitelists or DNS
Q: Can I provide and manage my own Firewall / Layer 3 for DRaaS?A: Yes! We’ll rack your Customer Provided Equipment (CPE) for DRaaS at no extra cost! This allows you the complete ability to manage NAT / Security / Client VPN during failoverBusiness Continuity Terms
3-2-1 Rule
- Three (3) copies of protected Data on at least two (2) different storage devices with one (1) copy located at a secure remote location such as VMsources Secure Cloud
Antivirus
- Antivirus products continually scan for known Virus Signatures on protected systems.
- Antivirus systems can not protect against new vectors (Signatures) which have not been published by the Antivirus vendor.
Auditing and Compliance
- Auditing and Compliance are the processes by which facilities and systems are compared against known standards by Qualified Auditors who then create reports which certify the facility or system is in Compliance with the standards used, or make note of exceptions.
Backup
- A Backup is an indexed archive of systems and data, usually compressed, and which needs to be Restore(d) prior to accessing the archived data.
Backup Copy
- A Backup Copy job sources a (usually) Incremental Backup and copies the data to an alternate location. Backup Copy jobs are the normal source for Offsite Backup(s) and have the advantage of being non-disruptive if it takes many hours to transfer data to an Offsite location such as VMsources Secure Backups.
Backup Repository
- A random-access storage system which can be used as the primary target of a Backup.
Best Effort
- Best Effort represents resources which are not reserved or pre-assigned and may not be available in the event of greater than normal demands on Infrastructure, such as during a large regional Disaster event.
CDP
- Continuous Data Protection (CDP) is near-synchronous Replication of data from source to target.
Cloud Computing
- Cloud Computing provides ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.
Compute Resources
-
The resources required by the active state of a computing system while it is powered on (CPU and RAM).
CPU
-
Central Processing Unit (CPU) provides logic, controls I/O and performs all calculations based on information stored in RAM.
Datacenter
- A secure and audited location where Cloud Computing resources are housed.
Disk/vDisk/HDD
-
computer Disk (AKA: vDisk, Virtual Disk, Hard Disk, HDD, SSD) is a non-volatile, random-access storage system on which data is stored.
DR
- Disaster Recovery (DR) is the notion of how an Organization would recover following a Disaster such as physical loss of data (such as in a Fire), logical loss of data (such as in a Ransomware Event) or temporary loss of data (such as during a power outage).
DRaaS
- Disaster Recovery as a Service (DRaaS) is a combination of Service Levels which includes at least Secure Backup and Replication.
DR Plan
- A Disaster Recovery Plan is the written and documented procedure for an organization to recover during / following a disaster.
DR Test
- A Disaster Recovery Test is the execution of the DR Plan sufficient to demonstrate that the Organization could recover following a disaster.
Endpoint Protection
-
Endpoint Protection differs from Antivirus in that it looks for specific behaviors which represent suspicious activity on protected systems. When discovered, Endpoint Protection will isolate (“quarantine”) systems until reviewed by an authorized administrator.
- Some Endpoint Protection platforms are comprehensive enough to be considered to be complete Antivirus replacement, while others need to be used in conjunction with traditional Antivirus systems.
Failover
- The process by which Replicated VMs are powered on and prepared for use using alternate resources, such as at a DRaaS Datacenter.
Full Backup
- A Full Backup is an archive of protected data and systems which can exist on its own, without any other supporting files.
Grandfather-Son (GFS) Backup
- Long-term retention of full backups on a schedule (Weekly, Monthly, Yearly).
Hardened / Immutable Repository
- Veeam Hardened / Immutable Repositories are tested and proven by Cohasset Associates meeting the requirements for non-rewritable, non-erasable storage as specified by SEC 17a-4(f), FINRA 4511(c) and CFTC 1.31(c)-(d) – WORM Equivalency.
Hypervisor
- A platform which draws resources from its physical host hardware and allocates those resources to VMs which run as independent and isolated systems.
Incremental Backup
- An Incremental Backup utilizes one Full Backup followed by successive increments of the data which contain only the portion that has changed since the preceding Incremental Backup. When a Restore is needed, the restoration process requires the last Full Backup plus all the Incremental Backups until the point of restoration.
MFA
-
Multifactor Authentication (MFA) is a process which requires external validation, in addition to the username/password combination. The most common form of MFA is 2FA (2 Factor Authentication) which sends a “push” notification or uses a hardware hey in addition to the username/password combination to validate users.
Offsite
- To a geographically separated location, usually with a minimum distance requirement of 100 KM., but possibly much more depending on: Power Grids, Flood areas, Geologic earthquake zones and much more.
Onsite
- To the same location as active Workloads and mission-critical data.
Pool
-
Shared resources, such as IP addresses, CPU, RAM and Disk which are assigned Best Effort.
RAM
-
Random Access Memory (RAM) stores volatile data which can be accessed and changed frequently while a computer system is powered on.
Replication / Replica
- Replication provides a ready-to-run (immediately accessible) Replica copy of a Virtual Machine at an alternate location. The primary advantage of Replication is that Replicated systems require no Restore prior to being accessible.
Restore
- The process of extracting data from a Backup and placing that data in a location where it is accessible. The Restore process is often time-consuming, depending on the format of data and systems used.
Restore Points
-
A Restore Point is the state protected by a Backup Job each time it runs.
Retention Policy
-
Retention Policy is the number of Restore Points which will be kept.
RPO
- Replication Point Objective is the time between Replication cycles that occurs in Asynchronous Replication. When met, the RPO is the maximum period of data loss to be expected.
RTO
- Recovery Time Objective (RTO) is the amount of time for systems to be functional after a disaster, including the time required to update public DNS and other service pointers. RTO can vary from just a few minutes for DRaaS protected systems to many hours for systems which need to be restored from Secure Offsite Backup
S3 Object Storage
- S3 Object Storage systems may be deployed to retain bulk or long-term Backups which were created targeting a random-access repository. S3 Object Storage is not suitable for random-access or transactional data, and cannot be used as the first generation of a Full Backup or Incremental Backup because it does not support the locking and sharing mechanisms needed to maintain a single, accurately updated version of a file.
Secure Cloud
- Secure, on-demand and elastic Compute and Storage resources located in geographically diverse areas.
Server
-
A dedicated Compute resource, either physical or virtual, which provides resources or services to users to access remotely.
Server Room
-
A dedicated area where Servers and other Compute resources are housed. The primary difference between a Server Room and Datacenter is that the Server Room has not been Audited against standards (Such as AICPA, NIST, ISO) whereas the Datacenter is Audited and in compliance with those standards
VM
-
Virtual Machine (VM) any form of Compute resource which runs on a Hypervisor.
Worm
-
A Write Once Read Many (WORM) refers to media which cannot be changed after creation for purposes of auditing and/or protection from Ransomware.
PLEASE NOTE- Veeam Hardened / Immutable Repositories are tested and proven by Cohasset Associates meeting the requirements for non-rewritable, non-erasable storage as specified by SEC 17a-4(f), FINRA 4511(c) and CFTC 1.31(c)-(d) – WORM Equivalency..
-
 Are you overwhelmed by the idea of comprehensive security for your IT Infrastructure? Don't be. Let us help make security more sensible and clear.
Are you overwhelmed by the idea of comprehensive security for your IT Infrastructure? Don't be. Let us help make security more sensible and clear.
We place security at the heart of all operations. Not only did we pioneer a powerful "gateway-less" network design for our Secure Cloud and Business Continuity clients, our proven innovative design provides the bulletproof security of Private Cloud in a fully-managed environment.
Cloud Security relies on order, but that order must come from the intelligent application of principles and standards, as opposed to the endless creation of highly specific rules.
Let our team will assist your team in understanding the principals of ITSM Cloud Security and Vulnerability Management at a fundamental level.
Download our Intellegent Security PDF: View PDFWhat we do to protect Secure Cloud What we do to protect our Clients - Edge systems use DUO Multifactor Authentication
- Strong, randomized passwords for Infrastructure Systems, 24 random characters or longer
- Comply with NIST 800-63B Digital Identity Guidelines
- Use dedicated Business Continuity domain for Backup and Infrastructure Systems
- Use Crowdstrike endpoint protection
- Encrypt passwords and sensitive and proprietary data
- Apply Geo-IP Blocklists
- Impliment true DMZ zones for portals and wevservers
- True 3-2-1 Rule Backup Compliance
- Local backups provide fast access to data and are the first component of the 3-2-1 Rule
- Remote backups provide the second component of the 3-2-1 Rule
- Veeam Replicas provide the third component of the 3-2-1 Rule
- We use only Veeam Immutable repository technology
- Tested and proven by Cohasset Associates meeting the requirements for non-rewritable, non-erasable storage as specified by SEC 17a-4(f), FINRA 4511(c) and CFTC 1.31(c)-(d) – WORM Equivalency
- Backups are Encrypted in-transit and at-rest
- That means a Threat Actor will never be able to use your own data against you
- Backup Repositories exist on dedicated SAN and Networks
-
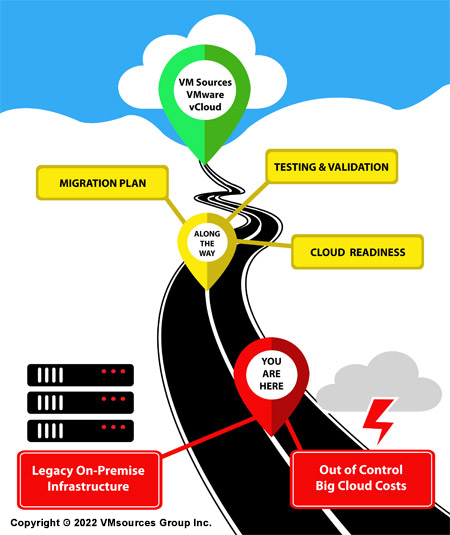 Are you hosting your own on-site IT Infrastructure and feel as though it's a never-ending battle of increasing costs and countless problems? Want something much better?
Are you hosting your own on-site IT Infrastructure and feel as though it's a never-ending battle of increasing costs and countless problems? Want something much better?
With our Secure Cloud, you can forget about managing hardware, firmware, VMware vSphere and storage, and turn your attention to higher value projects!VMsources Secure Cloud is now located in both the US-EAST and US-WEST compute zones allowing us to provide geographic low-latency and rapid DRaaS failover, all with guaranteed TCO and a 5 Nines SLA. Furthermore, you don’t need to choose just one zone, services can run concurrently on US-WEST and US-EAST.
VMsources Secure Cloud has two major advantages you will not find in the Big Cloud: Rapid Service Response and Guaranteed TCO. VMsources is already known for our unbeatable service and our guaranteed TCO means that you will know what your Cloud will cost for the life of the contract, and if you grow, you will know what that will cost as well!
Few organizations actually prepare or receive a true Roadmap to the Cloud before beginning a migration. As a result, Big Clouds end up costing hundreds of percent more than anticipated.
Let VMsources create a free Roadmap to our Secure Cloud, detailing every step along the way along with the results you will achieve when you arrive. Will be sure to assess your current systems for readiness, create and implement a fully managed migration plan, and then test and validate your systems before going into production with a guaranteed 36 month TCO!
Plan for the future of ITSM in your orginization with a free Roadmap to the VMware vCloud.- Cloud Readyness Assessment (Current systems, networking and Security)
- SLA requirements analysis
- Accurate quote and guaranteed TCO for your environment on our VMware vCloud
- Detailed Migration plan (that VMsources will manage fully if you chose our vCloud)
- Testing and Validation of your systems in the Cloud and proior to production
- Full transition to the VMware vCloud for production workload.

